How SAST Enhances Product Security at Egnyte
In today's fast-paced software development environment, security can no longer be an afterthought. Product security aims to embed security at every stage of the development lifecycle, and Static Application Security Testing (SAST) plays a crucial role in this process. By scanning source code early in the pipeline, SAST helps developers catch security issues before they reach production. In this blog, we'll explore how SAST enhances the security of software products and why it's essential for modern software development.
What Is SAST and How Does It Work? What Problems Does It Address?
SAST is a critical security testing technique that analyzes source code without executing it. By examining the code at rest, SAST identifies various security risks, including SQL injection, cross-site scripting (XSS), and other findings within the codebase. SAST tools can analyze code at very early stages of code production. They can scan existing code in the repository, be run at the stage of adding new changes to the code, and even run at the Integrated Development Environment (IDE) level. This near-real-time detection allows for quick response from developers and threat removal in a fast and non-blocking continuous integration and continuous delivery (CI/CD) way, ultimately leading to more secure applications with reduced remediation costs.
From a DevSecOps perspective, SAST embodies the shift-left approach, emphasizing the integration of security throughout the development lifecycle. By integrating security measures into the CI/CD pipeline, tools like SAST enable regular code scans for security findings during each build cycle. This allows developers to identify and fix issues early, before deployment.
Applying this approach also increases the efficiency of security-risk resolution within the service-level agreement (SLA). Developers can receive information about potential issues before they reach the main repository, significantly enhancing the efficiency of SLA fulfillment. In many cases, there is no need to measure SLA since the risk doesn't have time to materialize in the main code.
Another advantage of SAST is addressing regulatory requirements. All security standards (for example, NIST, OWASP, ISO 27001, HIPAA) require well-defined and effective vulnerability management processes. SAST is a key element due to its efficiency and enforcement of the shift-left approach.
Challenges in Implementing SAST
Implementing SAST brings numerous benefits, such as efficient detection of potential findings at the code level. However, to effectively make use of the benefits of SAST, one must consider a few challenges when integrating the process of static analysis into our pipelines and organizational culture. When implementing SAST, it's important to focus on the following aspects:
- Bad developer experience: One of the major challenges in implementing SAST is the poor developer experience. Complex user interfaces, unclear messages, lack of proper documentation, and the inability to integrate with existing development processes can discourage developers from using the tool effectively. This can lead to frustration, delayed adoption, and missed findings, ultimately reducing the overall effectiveness of the security testing process.
- Overly complex rules and false positives: SAST tools often come with a multitude of predefined rules that can generate an overwhelming number of false positives. This noise can distract developers, making it difficult to prioritize genuine security issues.
- Misalignment with technology stack: Many SAST tools provide rules that may not align well with the specific technologies used in a project. This misalignment can result in ineffective scans and missed security risks, ultimately reducing the effectiveness of the security measures.
- Absence of custom rules: The inability to create custom rules can hinder the effectiveness of SAST. Without tailoring rules to fit the unique context of the application, organizations risk overlooking critical security risks that could be easily identified with more relevant criteria.
- SAST deployment gets stale: As technologies used by developers constantly evolve, tools like SAST must keep up to remain useful. However, companies often stop investing heavily in product development once a "Good Enough" level is reached, which can reduce usability, leading to developers' reluctance to use the product.
By recognizing and addressing these challenges, teams can enhance their SAST implementation, thereby improving the overall security posture of their applications.
Implementing SAST at Egnyte: A Practical Example
Maintaining high-security standards across all codebases is challenging due to the rapid pace of software development and growing complexity. Such challenges lead to a fast-growing and evolving codebase. To address this, we implemented an automated and scalable solution to continuously monitor new code for security issues, streamline the review process, and empower developers to take ownership of security findings.
Our SAST process is currently built on Semgrep. We chose this tool due to its flexibility in integrating with our technology stack. Moreover, this tool addresses our implementation challenges to the greatest extent.
Here's how we approached the problem and successfully implemented SAST as a core part of our development pipeline.

Strategy
The key value of the SAST process is the shift-left in development. However, this doesn't mean the process is entirely transferred to developers. For SAST to be effective, the security team is a key contributor to the SAST process. The Egnyte Product Security team, which owns SAST, maintains and optimizes the entire process and tool so developers receive essential insights. This optimization involves careful analysis of needs, fine-tuning rules, and regularly consulting with developers about all findings. This crucial part of the process ensures developers focus on SAST findings to bring as much value as possible.
Just-in-Time Value for Devs: Diff Scans and Merge-Request Comments
A key part of implementing SAST is the introduction of diff scans in our merge request process. These scans focus on the code changes that are merged into the main branch. If any security issues are detected during this scan, Semgrep automatically generates a comment directly in GitLab. This integration allows developers to review and triage security issues within the same environment immediately they're already working in without needing to switch between multiple tools.
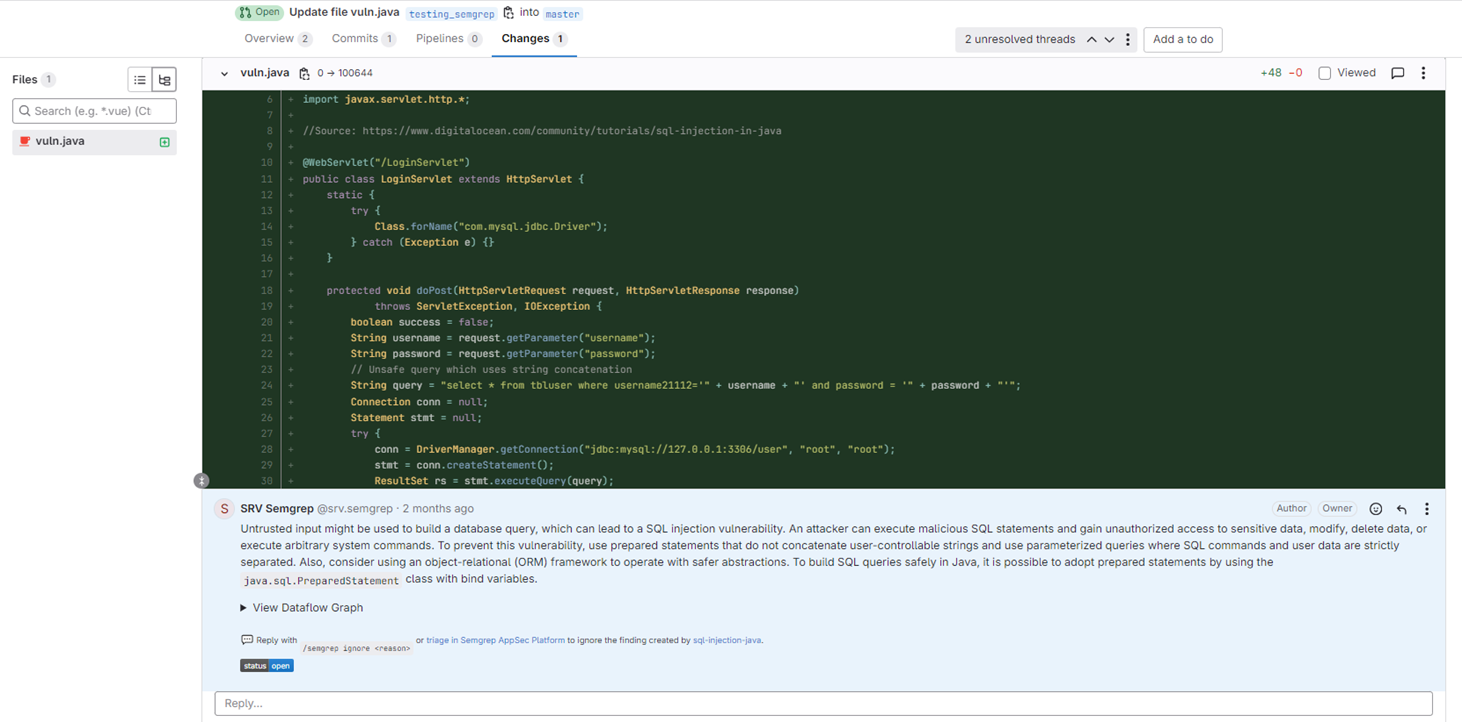
This streamlined process helps developers address security risks faster and more effectively, improving the project's overall security posture. The value is delivered directly to developers in their existing environment, GitLab, allowing them to address security issues without leaving their workflow. In addition, these automated comments act as another layer of remediation, reducing the risk of introducing new security issues into the existing codebase by catching them early in the merge process.
Base Scans
In addition to the previously described diff scans, we also conduct continuous base scans to thoroughly analyze the entire codebase for findings, including changes that the diff scans may have missed. These daily scans focus on the main code branches and use the SSDLC flag to identify which repositories need scanning. This ensures that the core of each project is continuously monitored for security risks, providing an additional layer of security for our existing code.
Continuous Improvement Cycle
Automating the process isn't everything. We believe that every process can be continuously improved, so we equipped our SAST process with a cyclical auditing mechanism aimed at analyzing and identifying areas for enhancement. Every month, members of our product security team thoroughly review the SAST process. This includes:
- Assessing metrics and evaluating developers' effectiveness in addressing issues.
- Identifying potential improvements to enhance the overall process.
- Reviewing items that haven't been addressed to determine if they might be false positives.
- Fine-tuning the rule sets by adding new rules, adjusting reporting modes, or disabling those that generate unnecessary noise (false positives).
We also stay updated with new Semgrep rule sets introduced by the community or created internally, ensuring that our scans remain accurate and comprehensive as new threats and coding patterns emerge. We’re also open to feedback from developers and will make changes in accordance with their suggestions.
Developer Training and Knowledge Sharing
A vital part of the SAST implementation was ensuring all developers were comfortable with the tools and processes. We conducted training sessions to introduce teams to Semgrep, explain how to interpret findings and demonstrate how to triage issues directly in GitLab. We also created detailed internal documentation to serve as a resource for new developers or those unfamiliar with the system.
This proactive approach ensures that security is not just a responsibility of the security team but is embedded into Egnyte’s development culture, making every developer an active participant in maintaining secure code.
As awareness of SAST increases, the goal is for developers to gradually take ownership of the tool, for example, by adding custom rule sets. This approach is desirable and indicates a high maturity level of the whole process.
Summary
Static Application Security Testing (SAST) is fundamental to the philosophy of DevSecOps, enabling the early detection and remediation of security issues during the application development phase. Integrating SAST into the CI/CD pipeline allows for the automation of security testing, which enhances code quality and minimizes the risk of introducing security risks into production. However, effective SAST implementation requires not only the right tools but also the awareness and commitment of the entire engineering organization.
By implementing SAST within DevSecOps, organizations can significantly enhance application security, minimizing technical debt and increasing engineering velocity through the availability of solutions before their complexity increases.